Microcorruption Security CTF
Matasano Security, who are world-renowned experts in information security and vulnerability analysis, recently released a Capture the Flag contest, where you assume the role of a hacker and attempt to break a series of physical warehouse locks controlled by microcontrollers, all by using reverse engineering.
I’m a sucker for reverse engineering games (for my own enjoyment only!) I recently got so frustrated with a “real-life treasure hunt” tablet game on iOS and Android that I spent countless hours breaking it with IDA Pro — which was a lot more fun than actually playing the game.
The Matasano Security CTF game, called microcorruption.com, is more than just fun, though. It serves as a reminder that the embedded devices that surround us, from office key cards to smart toys, wearable electronics and of course the ever-present smartphones, may have vulnerabilities that can lead to some pretty serious problems.
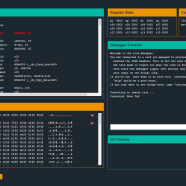
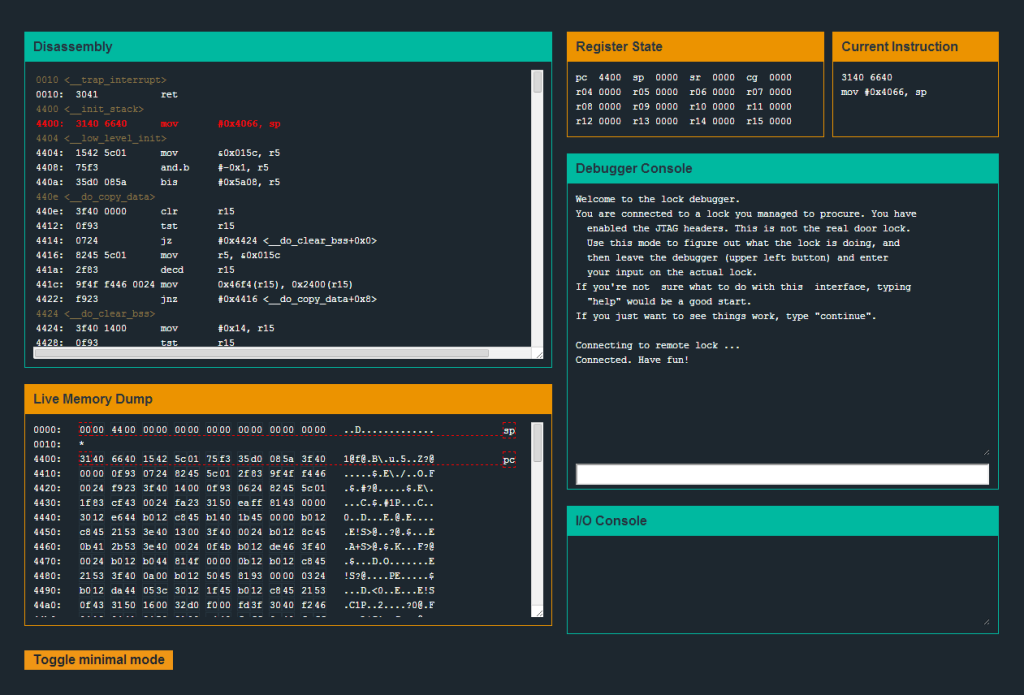
Here’s how the game works: You get access to a lock device, the disassembly of its code, and a low-level debugger and assembler. It’s all virtual of course, and you interact with it all via a simple web interface:
At each level, you’ll get a simple input that, owing to some C software bug, can be used to break the lock. You’ll use the debugger to reverse the target, find the input, and then deliver it to a “production” instance to beat the level.
You’ll face a series of revisions of the target, starting from “comically broken” and proceeding vendor-fix by vendor-fix through basic memory corruption, stack overflows, randomization, memory protection schemes, allocator vulnerabilities, and DRM-style software protection.
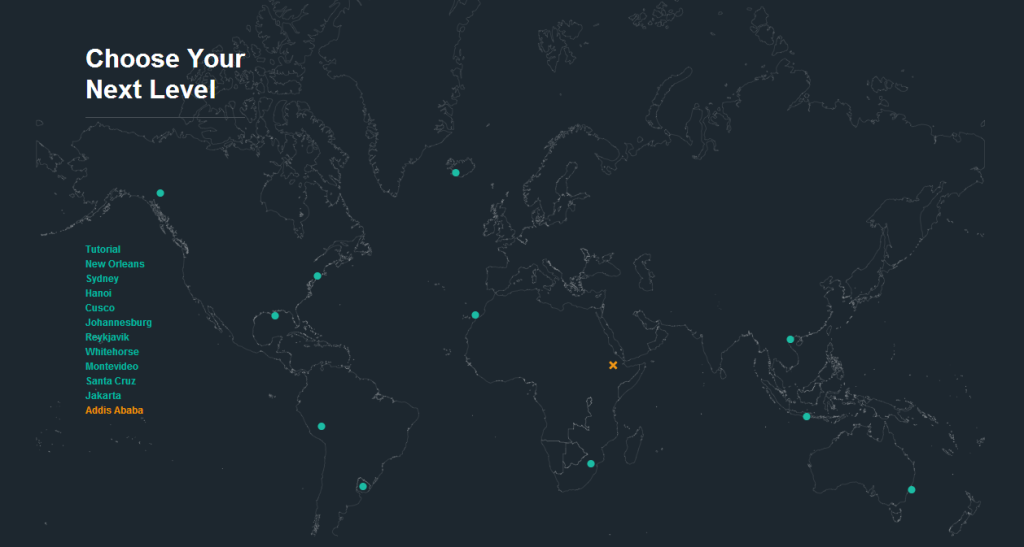
The game of course keeps track of your progress on a hacker-esque world map:
So far, I have broken 10 locks and have had to resort to many different kinds of buffer overflow tactics, injected hand-written assembly code and exploited undocumented features that I discovered simply by trying to anticipate how the device was designed. I’ve felt an immense sense of accomplishment as I own each lock. In one sense, it gets harder for each lock because the difficulty level is ramped up (it’s a game after all). But in another sense, it gets easier because you begin to know what to look for and your brain automatically starts devising evil plans for world domination.
But it’s not just fun and games. The code in each of the locks looks exactly like I would expect code in a “smart lock” to look like and the vulnerabilities are obscure. And that’s of course because this kind of code is written by people like you and me. We try to use appropriate patterns and cover all the bases but sometimes we inevitably leave unintended cracks in the code, under pressure from tight deadlines and budget constraints. And so the last line of defense becomes security through obscurity, and that never ever works in real life — because real-life hackers have more free time on their hands than you can even begin to imagine (especially if you have three kids).
In a web application, a bug is usually that a user can’t sign in or maybe get an occasional wrong price quoted. It’s typically not that big of a big deal, and it’s usually easy to investigate and fix. But in embedded systems, the consequences can be far more serious and much harder to remedy.
Imagine other people being easily able to not just circumvent your office key card locks by simply entering a series of digits on a keypad but also record employees’ data. Or take control of hospital devices that dispenses medicine. Or continuously send your biometric wrist bracelet GPS coordinates to China. And so on.
The devices that surround us are prone to vulnerabilities that can have serious consequences. The more developers know how devices work and how they can be exploited, the further down the road to implementing better and more secure code we are. So sign up on microcorruption.com and capture the flag!






I have been attending the the event too but i have absolutely no idea what you said stack overflows, randomization, memory protection schemes, allocator vulnerabilities, and DRM-style software protection and assembly injection. I am not complaining but i manage to get to Hanoi by looking at the instruction flows. problem is that i don’t know what to do to know?
I am not saying that you spoil it but can you give me a slight idea about the technique it involve.
The difficulty increases and the techniques you will need to employ changes as you progress, but looking at the instruction flow is important in all the scenarios. Sometimes it’s also important to understand very specific details about what each instruction does.
Hanoi is a good example of a simple buffer overflow exploit. Look at what happens right after the characters “Testing if password is valid.” is output to the console. Hint: What’s special about memory address 0x2410?
I have already see we are compairing if there is b6 stored at 0x2410 , i’ve been able to unlock the door but how do i guess the password.
And what in the world is buffer overflow i can google it but i need a little hint on how do i employ it.
The objective is to open the lock, the password is in this scenario irrelevant. Buffer overflow is the technique you use, filling in more data into the password buffer than was intended by the programmer. Wikipedia actually has a nice article about it: http://en.wikipedia.org/wiki/Buffer_overflow
Thank you for your courtesy
I read it and i get a idea of buffer overflow i get over Hanoi after using it. Thank you again.
Now i am on Cusco.
Hi , I have played this game and have trouble at Cusco. So can you give me a idea/hint to pass it. I thought may use buffer overflow to overwritten -0x4(r4) at function, but I don’t know how to do it.
Hi Mark — I’m a little bit on the fence about helping/hinting because the whole point is to come up with clever solutions yourself after analyzing carefully what goes on inside the locks. If you can figure out Cusco by yourself, you stand a much higher chance of breaking Johannesburg, and so on. So my first advice is to give it an extra hour. If you then really want help, please send me a message (email or fill out contact form) and I’ll reply!